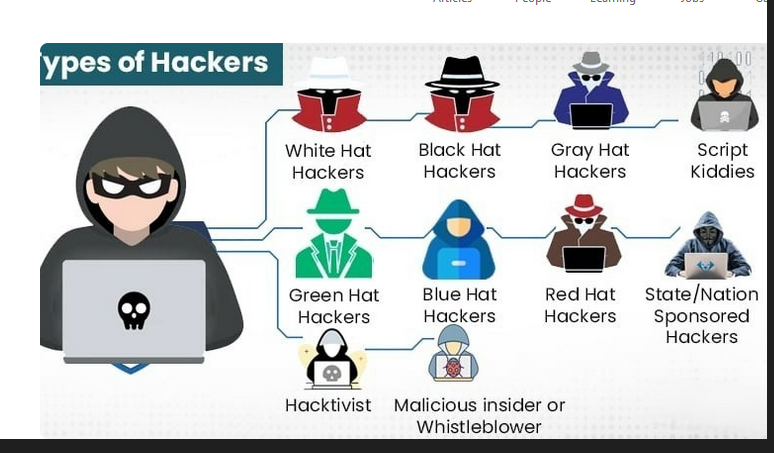
Hacker Types: Black Hat, White Hat, and Gray Hat Hackers
Who is hacker?
A computer hacker divided into many part according to skilled expert who overcome a problem using their technical knowledge.
black hat hacker

A dark blackhat programmer is a person who participates in unlawful or exploitative exercises including PC frameworks and organizations. Dissimilar to moral programmers, who expect to further develop security and safeguard frameworks, dark cap programmers exploit weaknesses for individual increase or malignant plan. Here is a more critical gander at what characterizes a dark cap programmer:

FAQ: White Hat Hackers
How do white hat hackers differ from black hat hackers?
What skills are necessary to become a white hat hacker?
What certifications are useful for white hat hackers?
How do white hat hackers get permission to test systems?
What are the typical tasks performed by white hat hackers?
Are white hat hackers legal?
Can white hat hackers find vulnerabilities that are later exploited by malicious hackers?
How do white hat hackers stay ethical in their work?
How can someone become a white hat hacker?
Define
A white hat software engineer is someone enrolled legally to test an affiliation’s or on the other hand person’s PC structures for shortcomings. They direct legitimate and moral hacking, with approval to enter security structures and further foster web-based insurance.
The expression “white cap” comes from old Western films, where the “heroes” wore white caps, representing their legitimate and moral activities. Many white caps are previous dark cap programmers who progressed to lawful hacking because of multiple factors.
Not by any stretch of the imagination like other cybercriminals, white covers help relationship with performing shortcoming assessments and illuminate the associations responsible for making patches of any weaknesses. Instead of hacking for information and individual or political expansion, white cap developers break into systems to augment security and reduction harmful attacks.
Gray hat hacker

A grey hat programmer is a person who takes part in hacking exercises without unequivocal proprietor’s consent however with non-noxious aim. These people mean to distinguish and uncover weaknesses in PC frameworks or organizations to assist associations with working on their security.
FAQ: gray hat hacker?:
What is a gray hat hacker? How do gray hat hackers differ from white hat and black hat hackers? What motivates gray hat hackers? What are the risks associated with gray hat hacking? How do gray hat hackers typically operate? What should a gray hat hacker do if they find a vulnerability? Is gray hat hacking legal? How can gray hat hackers improve their practices? Can gray hat hackers transition to white hat roles? What resources are available for gray hat hackers?
script kiddie hacker
A substance youth, skript young person, skiddie, young person, or slide is an unskilled individual who uses scripts or undertakings made by others, essentially for harmful purposes.
FAQ: Script Kiddies
What is a script kiddie?
How do script kiddies differ from other hackers?
What motivates script kiddies?
Are script kiddies a significant threat to cybersecurity?
. How can organizations protect against attacks by script kiddies?
What skills do script kiddies typically lack?
What skills do script kiddies typically lack?
What are the legal implications for script kiddies?
What are the legal implications for script kiddies?
How can script kiddies transition to ethical hacking roles?
What resources are available for those interested in ethical hacking?
Red hat hacker
Red cap programmers: These moral programmers effectively recognize and fix weaknesses in frameworks, like white cap programmers yet frequently with a more forceful methodology.
Green Hat hacker
Green hat hackers: These are novice hackers who are new to hacking and still learning the ropes, often experimenting with tools and techniques without much experience.
Blue hat hacker
Blue cap programmers: These people are recruited by associations to mess with test another product or framework network before it’s delivered. Their job is to find escape clauses or security weaknesses in the new programming and cure them before it dispatches.
Yellow hat hacker
Yellow cap programmers: These programmers — otherwise called virtual entertainment programmers — for the most part work via web-based entertainment. They utilize their abilities for both great and awful purposes, contingent upon the circumstance or their own advantages.
FAQ: Yellow Hat Hackers
What is a yellow hat hacker?
How do yellow hat hackers differ from other types of hackers?
What motivates yellow hat hackers?
Are yellow hat hackers legal?
What ethical considerations apply to yellow hat hackers?
How can yellow hat hackers transition to more recognized roles?
What are the potential risks of being a yellow hat hacker?
What can organizations do to address issues identified by yellow hat hackers?